Our Digital World - Part 1
- 0 Comments
- May 13, 2017
- by admin
- Technical Instruction
- Leave a comment
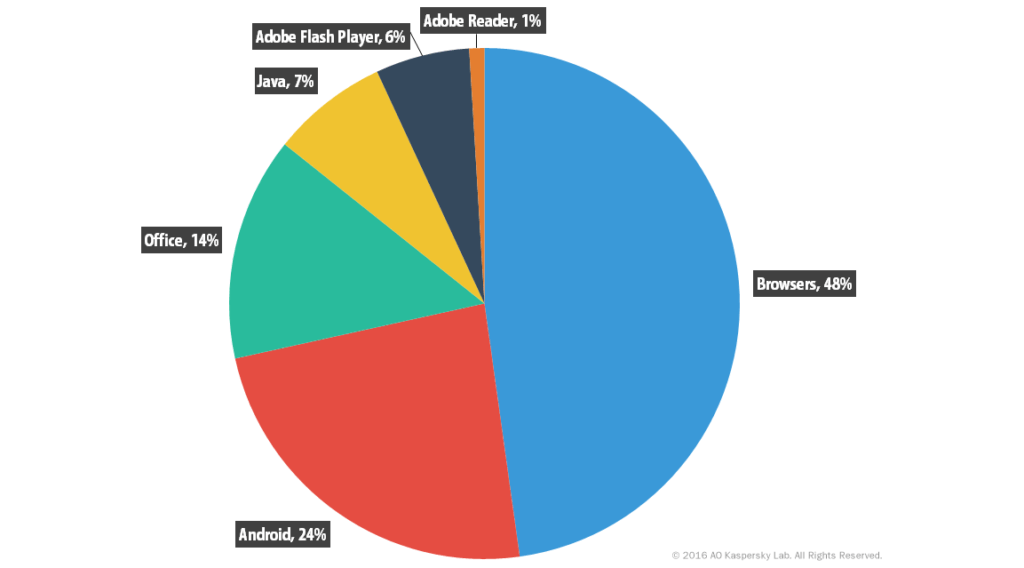
Something we have been wanting to do for a while now is a series of posts regarding different computer infection types, what they do, and how to avoid them. We briefly touched on this with our last Facebook post talking about recent phishing email scams, but wanted to go a little bit further on the subject to help our clients. This post will be an introduction to the series to try and let you know what we will be covering. Some of you will likely be familiar with terms used in the series and some may not, if you would like me to clarify or delve deeper into a specific topic please reply on Facebook, comment on the post at our site, or give us a call. So in getting started the types of infections we will go into are: Spyware, Malware, Adware, Phishing, Trojans, Worms, and Ransomware. We will also get into our experience based opinions on Antivirus software and their real world effectiveness. Let's start off with some statistics: In Q2 (April through June) 2016, One Antivirus Company detected 3,626,458 malicious installation packages, an increase of 1.7x over Q1 (January through March). Infections are not limited to just laptop and desktop users, in Q2 2016, they detected 83,048 mobile Trojan-Ransomware installation packages, which is about the same number as the previous quarter and seven times more than in Q4 2015. Here is a graph indicating what applications were most exploited to allow malicious activity in Q2 2016.
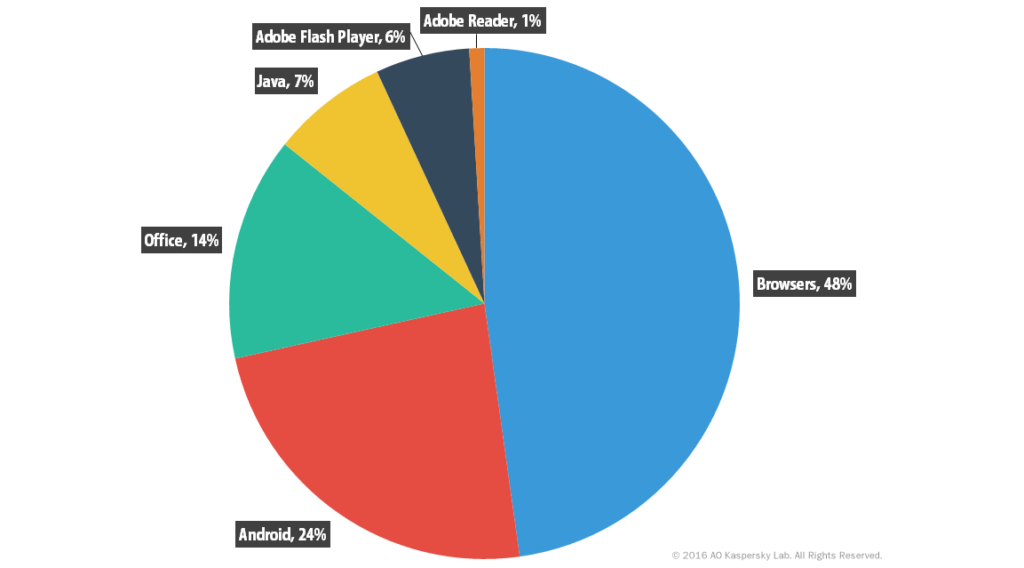
You can see from the above that one of the things you can do to protect yourself is to keep your applications and browsers up to date. However there are pitfalls here as well, attackers know this information as well and will try (sometimes very convincingly) to get you to click on their software under the ruse that you need an update to a specific software. You need to understand that the people who do this are very smart and it is not just some lazy kid in their parents basement creating this stuff, these are the images the professional attackers want you to conjure as it affords them a type of cloaking, letting you think this is some dumb kid and it will pass. I can assure you that this will not just pass and will require you to be very attentive while online to avoid their attacks.
I know this is a lot to take in but trust me, armed with the information I will be going over in the future posts of this series, you will be better prepared to protect yourself from some of the nastiest infections the internet has to offer.

0 Comments